SCADA, Supervisory Control and Data Acquisitions, are computer systems that control various real-world equipment. These machines are crucial parts of production lines, power plants and nuclear facilities. They were relatively unknown, even to information security experts, that was until Stuxnet was detected. Stuxnet, a malware supposedly developed by the United States and Israel, targeted SCADA systems in Iran’s Natnaz nuclear facility. By infecting the control systems, the malware was able to spin nuclear fuel enrichment centrifuges out of control and cause major damage to Iran’s nuclear efforts until Stuxnet’s detection. After its detection, SCADA became one of the most talked about subjects in cyber security. Stuxnet made everyone realize that cyber attacks can have a impact on the real world – and because of that they are major targets to attackers.
Now, access to such compromised systems is being sold in the underground economy.
A fraudster has recently posted in several underground forums that he is selling access to SCADA systems. Concerned that many criminals will not understand what’s being offered for sale, he started his post with the Wikipedia definition of SCADA. Afterwards, trying to bank on recent news, he noted they would be perfect for “duqu 2.0” (a recently discovered malware which was most likely developed by a country to spy on the Iranian Nuclear talks).

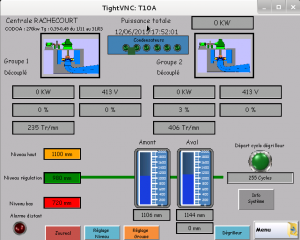
As the underground is filled with fraudsters who make bogus claims in attempts to rip off interested buyers, the fraudster posted proof that he truly does have access to such systems – a screen shot from a supposedly compromised SCADA system. The screen shot appears to be from a SCADA system in France, which might be part of some hydro-electric generator.

In a closed underground forum, the fraudster also shared three IP addresses and VNC passwords (remote desktop) to three SCADA systems, to further solidify his claims. All three IP addresses are also in France. Two of them are on Orange FR’s IP range and the third is on the IP range of Keyyo.
We haven’t attempted to connect to these systems and cannot validate the information.
So, is this the smoking gun security experts have been waiting for? are cybercriminals now joining forces with government hackers to take on SCADA systems, potentially causing harm in the real world? Most likely not, a single offering from a vendor does not constitute as a trend. However, assuming the vendor is not making these claims for the purpose of ripping off people, the fact that compromised SCADA systems are now offered for sale for anyone to purchase, including jihadists and hacktivists, should not be taken lightly. Even if it is the one vendor, at the moment, compromised SCADA systems are currently just a Bitcoin transfer away to anyone with access to these forums. If this would turn into a trend, and only time would tell if it does, vulnerable SCADA systems would become much more available to interested attackers, including ones who are not technically capable.
About the Author: Idan Aharoni is the founder & CEO of Inteller, a leading provider of web intelligence solutions. Idan was the Head of Cyber Intelligence at RSA where he was responsible for gathering, analyzing and reporting intelligence findings on cybercrime and fraud activity. Idan joined Cyota (later acquired by RSA) in February 2005 as an analyst at the Anti-Fraud Command Center. In 2006, he founded the FraudAction Intelligence team, which he led until 2013. Between his work at the Anti-Fraud Command Center, as well as the unique insight he has gained by the intelligence and discoveries gathered by his team at RSA, Idan offers vast expertise into the underground fraud economy and how cybercriminals operate. Cross Posted From Inteller Solutions Blog