Geanonimiseerde gegevens blijken toch niet zo anoniem
 Onderzoekers van Universiteit Leuven en het Imperial College Londen hebben ontdekt dat het de-anonimiseren van geanonimiseerde datasets makkelijker is dan tot voor kort werd aangenomen . Ze hebben dit aangetoond door middel van een model dat schat hoe makkelijk het is om een dataset te de-anonimiseren. Geanonimiseerde gegevens worden overal voor gebruikt: medisch onderzoek, gepersonaliseerde aanbevelingen en moderne AI-technieken. De veronderstelling is dat alle persoonlijke identificeerbare informatie verwijderd is terwijl een kern van de nuttige informatie voor onderzoekers behouden blijft. Zo heeft een ziekenhuis de mogelijkheid om de namen, adressen en geboortedata van patiënten te verwijderen uit een set […] […]
Onderzoekers van Universiteit Leuven en het Imperial College Londen hebben ontdekt dat het de-anonimiseren van geanonimiseerde datasets makkelijker is dan tot voor kort werd aangenomen . Ze hebben dit aangetoond door middel van een model dat schat hoe makkelijk het is om een dataset te de-anonimiseren. Geanonimiseerde gegevens worden overal voor gebruikt: medisch onderzoek, gepersonaliseerde aanbevelingen en moderne AI-technieken. De veronderstelling is dat alle persoonlijke identificeerbare informatie verwijderd is terwijl een kern van de nuttige informatie voor onderzoekers behouden blijft. Zo heeft een ziekenhuis de mogelijkheid om de namen, adressen en geboortedata van patiënten te verwijderen uit een set […] […]Ransomware and the enterprise: A new white paper
 Throughout 2018 criminals have continued to target large organizations with ransomware. Today we introduce a new white paper that explains why ransomware is still a serious threat to your organization – regardless of size – and what can be done to reduce exposure to, and damage from, ransomware attacks. The paper focuses on three particularly dangerous ransomware attack vectors: remote access, email, and supply chain. The paper is intended to help CEOs, CIOs, CISOs, and enterprise risk managers understand the current state of the ransomware threat as well several evolving areas of concern. The more technical aspects of ransomware […] […]
Throughout 2018 criminals have continued to target large organizations with ransomware. Today we introduce a new white paper that explains why ransomware is still a serious threat to your organization – regardless of size – and what can be done to reduce exposure to, and damage from, ransomware attacks. The paper focuses on three particularly dangerous ransomware attack vectors: remote access, email, and supply chain. The paper is intended to help CEOs, CIOs, CISOs, and enterprise risk managers understand the current state of the ransomware threat as well several evolving areas of concern. The more technical aspects of ransomware […] […]Before Using Birth Control Apps, Consider Your Privacy
 Hotlittlepotato Score one for the quantified self-surveillance movement. Last week, the US Food and Drug Agency approved the first-ever, over-the-counter digital contraceptive—a polished and almost preternaturally upbeat mobile app called Natural Cycles . Basal body temperature readings and monthly menstruation data feed into an algorithm that tells users whether or not they should be having unprotected sex. Like most forms of birth control, it’s not foolproof ; the app has been dogged by reports of unwanted pregnancies that prompted two ongoing investigations by European authorities into its Swedish maker’s marketing claims. But that hasn’t hurt Natural Cycles’ popularity. The […] […]
Hotlittlepotato Score one for the quantified self-surveillance movement. Last week, the US Food and Drug Agency approved the first-ever, over-the-counter digital contraceptive—a polished and almost preternaturally upbeat mobile app called Natural Cycles . Basal body temperature readings and monthly menstruation data feed into an algorithm that tells users whether or not they should be having unprotected sex. Like most forms of birth control, it’s not foolproof ; the app has been dogged by reports of unwanted pregnancies that prompted two ongoing investigations by European authorities into its Swedish maker’s marketing claims. But that hasn’t hurt Natural Cycles’ popularity. The […] […]How to Protect Yourself Against a SIM Swap Attack
 Casey Chin A spate of hacked Instagram accounts. A $220 million lawsuit against AT&T. A bustling underground crime ring . They all have roots in an old problem that has lately found new urgency: SIM card swaps , a scam in which hackers steal your mobile identity—and use it to upend your life . At its most basic level, a SIM swap is when someone convinces your carrier to switch your phone number over to a SIM card they own. They’re not doing it for prank call cover, or to rack up long-distance charges. By diverting your incoming messages, […] […]
Casey Chin A spate of hacked Instagram accounts. A $220 million lawsuit against AT&T. A bustling underground crime ring . They all have roots in an old problem that has lately found new urgency: SIM card swaps , a scam in which hackers steal your mobile identity—and use it to upend your life . At its most basic level, a SIM swap is when someone convinces your carrier to switch your phone number over to a SIM card they own. They’re not doing it for prank call cover, or to rack up long-distance charges. By diverting your incoming messages, […] […]Smart irrigation systems vulnerable to attacks, warn researchers
 Security researchers have warned of a potential attack that – using a “piping botnet ” of internet-connected irrigation systems that water simultaneously – could impact a city’s water system to the point of actually draining its reserves. A team of six academics from Ben-Gurion University of Negev, Israel, identified and analyzed security flaws in the firmware of several commercial irrigation systems that are connected to the internet. They focused on three commonly sold smart irrigation systems – GreenIQ, BlueSpray, and RainMachine – and found that they suffer from vulnerabilities that enable attackers to remotely turn watering systems on and […] […]
Security researchers have warned of a potential attack that – using a “piping botnet ” of internet-connected irrigation systems that water simultaneously – could impact a city’s water system to the point of actually draining its reserves. A team of six academics from Ben-Gurion University of Negev, Israel, identified and analyzed security flaws in the firmware of several commercial irrigation systems that are connected to the internet. They focused on three commonly sold smart irrigation systems – GreenIQ, BlueSpray, and RainMachine – and found that they suffer from vulnerabilities that enable attackers to remotely turn watering systems on and […] […]Signature Validation Bug Let Malware Bypass Several Mac Security Products
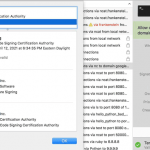 A years-old vulnerability has been discovered in the way several security products for Mac implement Apple’s code-signing API that could make it easier for malicious programs to bypass the security check, potentially leaving millions of Apple users vulnerable to hackers. Josh Pitts, a researcher from security firm Okta, discovered that several third-party security products for Mac—including Little Snitch, F-Secure xFence, VirusTotal, Google Santa, and Facebook OSQuery—could be tricked into believing that an unsigned malicious code is signed by Apple. Code-signing mechanism is a vital weapon in the fight against malware, which helps users identify who has signed the app […] […]
A years-old vulnerability has been discovered in the way several security products for Mac implement Apple’s code-signing API that could make it easier for malicious programs to bypass the security check, potentially leaving millions of Apple users vulnerable to hackers. Josh Pitts, a researcher from security firm Okta, discovered that several third-party security products for Mac—including Little Snitch, F-Secure xFence, VirusTotal, Google Santa, and Facebook OSQuery—could be tricked into believing that an unsigned malicious code is signed by Apple. Code-signing mechanism is a vital weapon in the fight against malware, which helps users identify who has signed the app […] […]World’s biggest DDoS marketplace taken down, six suspected admins nabbed
 An international law enforcement operation has shut down a website widely thought to be the world’s biggest marketplace for hiring distributed denial-of-service ( DDoS ) attacks, according to an announcement by the United Kingdom’s National Crime Agency (NCA). The website, webstresser.org, was taken down on Wednesday, April 25, following […] .
An international law enforcement operation has shut down a website widely thought to be the world’s biggest marketplace for hiring distributed denial-of-service ( DDoS ) attacks, according to an announcement by the United Kingdom’s National Crime Agency (NCA). The website, webstresser.org, was taken down on Wednesday, April 25, following […] .AI Can Help Cybersecurity—If It Can Fight Through the Hype
 There are a ton of claims around AI and cybersecurity that don’t quite add up. Here’s what’s really going on. Walking the enormous exhibition halls at the recent RSA security conference in San Francisco, you could have easily gotten the impression that digital defense was a solved problem. Amidst […] .
There are a ton of claims around AI and cybersecurity that don’t quite add up. Here’s what’s really going on. Walking the enormous exhibition halls at the recent RSA security conference in San Francisco, you could have easily gotten the impression that digital defense was a solved problem. Amidst […] .Data Protection Standards Need to Be Global
 Broadly, customers around the world should be in charge of the information companies have about them, and companies need to be liable if they misuse it. Whether it is Cambridge Analytica gaining access to private information on up to 87 million Facebook users, or the large-scale data breaches at […] .
Broadly, customers around the world should be in charge of the information companies have about them, and companies need to be liable if they misuse it. Whether it is Cambridge Analytica gaining access to private information on up to 87 million Facebook users, or the large-scale data breaches at […] .This test will tell you how likely you are to fall for fraud
 Researchers have devised a test that gauges a person’s susceptibility to falling for online scams and other types of internet crime. The freely available questionnaire – called “ Susceptibility to Persuasion – II ” (StP-II) and developed by scientists at the Universities of Cambridge and Helsinki – asks the […] .
Researchers have devised a test that gauges a person’s susceptibility to falling for online scams and other types of internet crime. The freely available questionnaire – called “ Susceptibility to Persuasion – II ” (StP-II) and developed by scientists at the Universities of Cambridge and Helsinki – asks the […] .A New Cryptocurrency Mining Virus is Spreading Through Facebook
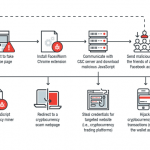 If you receive a link for a video, even if it looks exciting, sent by someone (or your friend) on Facebook messenger—just don’t click on it without taking a second thought. Cybersecurity researchers from Trend Micro are warning users of a malicious Chrome extension which is spreading through Facebook […] .
If you receive a link for a video, even if it looks exciting, sent by someone (or your friend) on Facebook messenger—just don’t click on it without taking a second thought. Cybersecurity researchers from Trend Micro are warning users of a malicious Chrome extension which is spreading through Facebook […] .Have we hit peak ransomware? Maybe, according to F-Secure
 Ransomware is really nasty. Once it’s infiltrated your system, it’ll place your crucial work files and cherished family photos out of reach, and demand a small fortune in Bitcoin for their return. Fortunately though, new research from Finnish security firm F-Secure suggests that this is a threat that’s hit […] .
Ransomware is really nasty. Once it’s infiltrated your system, it’ll place your crucial work files and cherished family photos out of reach, and demand a small fortune in Bitcoin for their return. Fortunately though, new research from Finnish security firm F-Secure suggests that this is a threat that’s hit […] .Amazon Key Lets Delivery People Into Your House—and It Just Got Hacked
 Today Amazon Key Lets Delivery People Into Your House—and It Just Got Hacked A key hardware safeguard in Amazon’s recently launched while-you’re-out delivery service has been hacked. And, well—less just say you probably should have seen this coming. Amazon Key uses a smart lock and cloud-based security camera in […] .
Today Amazon Key Lets Delivery People Into Your House—and It Just Got Hacked A key hardware safeguard in Amazon’s recently launched while-you’re-out delivery service has been hacked. And, well—less just say you probably should have seen this coming. Amazon Key uses a smart lock and cloud-based security camera in […] .Nederlandse kansspelautoriteit onderzoekt games met ‘lootboxen’
 Het is het laatste jaar een steeds groter wordende klacht bij gamers: lootboxen. Voor wie niet speelt: zie het als een pakje verzamelkaarten, met het verschil dat de kaarten iets doen in een game waar je als speler iets aan hebt. Dat varieert van cosmetische attributen zoals bijvoorbeeld een […] .
Het is het laatste jaar een steeds groter wordende klacht bij gamers: lootboxen. Voor wie niet speelt: zie het als een pakje verzamelkaarten, met het verschil dat de kaarten iets doen in een game waar je als speler iets aan hebt. Dat varieert van cosmetische attributen zoals bijvoorbeeld een […] .Another Shady App Found Pre-Installed on OnePlus Phones that Collects System Logs
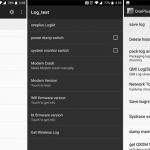 The OnePlus Saga Continues… Just a day after the revelation of the hidden Android rooting backdoor pre-installed on most OnePlus smartphones, a security researcher just found another secret app that records tons of information about your phone. Dubbed OnePlusLogKit , the second pre-installed has been discovered by the same […] .
The OnePlus Saga Continues… Just a day after the revelation of the hidden Android rooting backdoor pre-installed on most OnePlus smartphones, a security researcher just found another secret app that records tons of information about your phone. Dubbed OnePlusLogKit , the second pre-installed has been discovered by the same […] .Latest NSA Leak Reveals Exactly the Kind of Cyberattack Experts Had Warned About
 The details of an apparent Russian state-sponsored cyberattack on local election officials and a vendor of U.S. voting software are shocking—but they shouldn’t be surprising. In fact, experts had been warning for months before the 2016 election about exactly the type of attack that was revealed Monday in leaked […] .
The details of an apparent Russian state-sponsored cyberattack on local election officials and a vendor of U.S. voting software are shocking—but they shouldn’t be surprising. In fact, experts had been warning for months before the 2016 election about exactly the type of attack that was revealed Monday in leaked […] .Newly Found Malware Uses 7 NSA Hacking Tools, Where WannaCry Uses 2
 A security researcher has identified a new strain of malware that also spreads itself by exploiting flaws in Windows SMB file sharing protocol, but unlike the WannaCry Ransomware that uses only two leaked NSA hacking tools , it exploits all the seven. Last week, we warned you about multiple […] .
A security researcher has identified a new strain of malware that also spreads itself by exploiting flaws in Windows SMB file sharing protocol, but unlike the WannaCry Ransomware that uses only two leaked NSA hacking tools , it exploits all the seven. Last week, we warned you about multiple […] .The 5 most common online scams to watch for
 The internet can be a scary place. Misinformation, false promises, and fake news lurk behind every clickbait headline and questionable link. Entire industries are built to profit from deceptive tricks to con the naive […] .
The internet can be a scary place. Misinformation, false promises, and fake news lurk behind every clickbait headline and questionable link. Entire industries are built to profit from deceptive tricks to con the naive […] .Hackers Are Trying to Reignite WannaCry With Non-Stop Botnet Attacks
 Over the past year, two digital disasters have rocked the internet. The botnet known as Mirai knocked a swath of major sites off the web last September, including Spotify, Reddit, and the New York Times . And over the past week, the WannaCry ransomware outbreak crippled systems […] .
Over the past year, two digital disasters have rocked the internet. The botnet known as Mirai knocked a swath of major sites off the web last September, including Spotify, Reddit, and the New York Times . And over the past week, the WannaCry ransomware outbreak crippled systems […] .Another Ransomware Nightmare Could Be Brewing in Ukraine
 Just as the reverberations from last week’s WannaCry ransomware outbreak have started to slow, a new threat has already cropped up. A virulent ransomware strain called XData has gained momentum in Ukraine, so far leading to about three times as many infections as WannaCry did in the […] .
Just as the reverberations from last week’s WannaCry ransomware outbreak have started to slow, a new threat has already cropped up. A virulent ransomware strain called XData has gained momentum in Ukraine, so far leading to about three times as many infections as WannaCry did in the […] .More Hacking Groups Found Exploiting SMB Flaw Weeks Before WannaCry
 Since the Shadow Brokers released the zero-day software vulnerabilities and hacking tools – allegedly belonged to the NSA’s elite hacking team Equation Group – several hacking groups and individual hackers have started using them in their own way. The April’s data dump was believed to be the most damaging […] .
Since the Shadow Brokers released the zero-day software vulnerabilities and hacking tools – allegedly belonged to the NSA’s elite hacking team Equation Group – several hacking groups and individual hackers have started using them in their own way. The April’s data dump was believed to be the most damaging […] .Zomato Hacked; Hacker Puts Up 17 Million Users’ Emails and Passwords On Sale
 If you ever ordered food from Zomato, You should be Worried! India’s largest online restaurant guide Zomato confirmed today that the company has suffered a data breach and that accounts details of millions of its users have been stolen from its database. In a blog post published today, the […] .
If you ever ordered food from Zomato, You should be Worried! India’s largest online restaurant guide Zomato confirmed today that the company has suffered a data breach and that accounts details of millions of its users have been stolen from its database. In a blog post published today, the […] .Bell Canada Hacked: Data of 1.9 Million Customers Stolen
 While we all were busy in the WannaCry ransomware menace, two separate data breaches have been reported, one in DocuSign , a major provider of electronic signature technology, and another in BELL, Canada’s largest telecommunications company. Canadian mobile phone, TV, and internet service provider Bell on Monday confirmed that […] .
While we all were busy in the WannaCry ransomware menace, two separate data breaches have been reported, one in DocuSign , a major provider of electronic signature technology, and another in BELL, Canada’s largest telecommunications company. Canadian mobile phone, TV, and internet service provider Bell on Monday confirmed that […] .WannaCryptor wasn’t the first to use EternalBlue: Miners misused it days after Shadow Brokers leak
 The massive campaign that spread the WannaCryptor (aka WannaCry) ransomware wasn’t the only large-scale infection misusing the EternalBlue and DoublePulsar exploits, leaked by Shadow Brokers. The same mechanism has been misused by black hats as early as the end of April, when they opted for off-the-shelf Monero cryptocurrency mining […] .
The massive campaign that spread the WannaCryptor (aka WannaCry) ransomware wasn’t the only large-scale infection misusing the EternalBlue and DoublePulsar exploits, leaked by Shadow Brokers. The same mechanism has been misused by black hats as early as the end of April, when they opted for off-the-shelf Monero cryptocurrency mining […] .Latest Hacking Tools Leak Indicates NSA Was Targeting SWIFT Banking Network
 Latest Hacking Tool Leak Indicates NSA Was Targeting SWIFT Banking Network The Shadow Brokers – a hackers group that claimed to have stolen a bunch of hacking tools from the NSA – released today more alleged hacking tools and exploits that target earlier versions of Windows operating system, along […] .
Latest Hacking Tool Leak Indicates NSA Was Targeting SWIFT Banking Network The Shadow Brokers – a hackers group that claimed to have stolen a bunch of hacking tools from the NSA – released today more alleged hacking tools and exploits that target earlier versions of Windows operating system, along […] .Android Trojan Targeting Over 420 Banking Apps Worldwide Found On Google Play Store
 android banking malware Do you like watching funny videos online? I am not kind of a funny person, but I love watching funny videos clips online, and this is one of the best things that people can do in their spare time. But, beware if you have installed a […] .
android banking malware Do you like watching funny videos online? I am not kind of a funny person, but I love watching funny videos clips online, and this is one of the best things that people can do in their spare time. But, beware if you have installed a […] .Hackers Can Steal Your Passwords Just by Monitoring SmartPhone Sensors
 Do you know how many kinds of sensors your smartphone has inbuilt? And what data they gather about your physical and digital activities? An average smartphone these days is packed with a wide array of sensors such as GPS, Camera, microphone, accelerometer, magnetometer, proximity, gyroscope, pedometer, and NFC, to […] .
Do you know how many kinds of sensors your smartphone has inbuilt? And what data they gather about your physical and digital activities? An average smartphone these days is packed with a wide array of sensors such as GPS, Camera, microphone, accelerometer, magnetometer, proximity, gyroscope, pedometer, and NFC, to […] .Germany Bans Facebook From Collecting WhatsApp Data
 German Bans Facebook From Collecting WhatsApp Data Just last month, the most popular messaging app WhatsApp updated its privacy policy and T&Cs to start sharing its user data with its parent company, and now both the companies are in trouble, at least in Germany and India. Both Facebook, as […] .
German Bans Facebook From Collecting WhatsApp Data Just last month, the most popular messaging app WhatsApp updated its privacy policy and T&Cs to start sharing its user data with its parent company, and now both the companies are in trouble, at least in Germany and India. Both Facebook, as […] .Apple Tracks Who You’re Chatting Using iMessage — and Shares that Data with Police
 Doing conversations with your friend on iMessage and thinking that they are safe and out of reach from anyone else other than you and your friend? No, it’s not. End-to-end encryption doesn’t mean that your iMessages are secure enough to hide your trace because Apple not only stores a […] .
Doing conversations with your friend on iMessage and thinking that they are safe and out of reach from anyone else other than you and your friend? No, it’s not. End-to-end encryption doesn’t mean that your iMessages are secure enough to hide your trace because Apple not only stores a […] .In-Brief: Spotify Hack, Secret of Chrome OS, MIT Bug Bounty, Nanowire Batteries
 1. Spotify Hacked! Change your Password ASAP If you are one of the millions of people around the world who love to listen to music on Spotify, you may need to change your password immediately. Has Spotify been hacked? The company says no, but some Spotify users have claimed […] .
1. Spotify Hacked! Change your Password ASAP If you are one of the millions of people around the world who love to listen to music on Spotify, you may need to change your password immediately. Has Spotify been hacked? The company says no, but some Spotify users have claimed […] .Car Hacking ? Scary, But Now it’s REALITY!
 Next time you find yourself hooked up behind the wheel, make sure that your car is actually in your control. Hackers are now able to break into hundreds of thousands of vehicles on the road. Car hacking is a hot topic today and until now it was performed only […] .
Next time you find yourself hooked up behind the wheel, make sure that your car is actually in your control. Hackers are now able to break into hundreds of thousands of vehicles on the road. Car hacking is a hot topic today and until now it was performed only […] .Protecting Our Individual Freedoms in a Digital World
 PSFK talks to Nuala O’Connor about the importance of advocating for basic human rights in the online space PSFK talks to Nuala O’Connor about the importance of advocating for basic human rights in the online space Innovation is the new currency in today’s Idea Economy. In recognition of the […] .
PSFK talks to Nuala O’Connor about the importance of advocating for basic human rights in the online space PSFK talks to Nuala O’Connor about the importance of advocating for basic human rights in the online space Innovation is the new currency in today’s Idea Economy. In recognition of the […] .Panicked over massive data breach? You should be
 Government data breach affected more than 20 million 01:14 Douglas Rushkoff writes a regular column for CNN.com. He is a media theorist, the author of the book “Present Shock: When Everything Happens Now” and professor of media studies at the City University of New York’s Queens College. This commentary […] .
Government data breach affected more than 20 million 01:14 Douglas Rushkoff writes a regular column for CNN.com. He is a media theorist, the author of the book “Present Shock: When Everything Happens Now” and professor of media studies at the City University of New York’s Queens College. This commentary […] .Educating Citizens on Protecting Their Online Identities
 PSFK speaks to Nico Sell, co-founder of the world’s most secure peer-to-peer encrypted messaging system, about the perils of digital security PSFK speaks to Nico Sell, co-founder of the world’s most secure peer-to-peer encrypted messaging system, about the perils of digital security Innovation is the new currency in today’s […] .
PSFK speaks to Nico Sell, co-founder of the world’s most secure peer-to-peer encrypted messaging system, about the perils of digital security PSFK speaks to Nico Sell, co-founder of the world’s most secure peer-to-peer encrypted messaging system, about the perils of digital security Innovation is the new currency in today’s […] .SCADA Systems Offered for Sale in the Underground Economy
 SCADA, Supervisory Control and Data Acquisitions, are computer systems that control various real-world equipment . These machines are crucial parts of production lines, power plants and nuclear facilities. They were relatively unknown, even to information security experts, that was until Stuxnet was detected. Stuxnet, a malware supposedly developed by […] .
SCADA, Supervisory Control and Data Acquisitions, are computer systems that control various real-world equipment . These machines are crucial parts of production lines, power plants and nuclear facilities. They were relatively unknown, even to information security experts, that was until Stuxnet was detected. Stuxnet, a malware supposedly developed by […] .Charleston Shooting: Reactions On and Off Social Media
 Whenever tragedies such as the shooting at the Emmanuel AME church in Charleston, South Carolina occur, reaction on social media is swift. Aside from the fact that users on Twitter identified the suspect long before the FBI publicly identified him , social media seems to have become the platform […] .
Whenever tragedies such as the shooting at the Emmanuel AME church in Charleston, South Carolina occur, reaction on social media is swift. Aside from the fact that users on Twitter identified the suspect long before the FBI publicly identified him , social media seems to have become the platform […] .Edinburgh police force builds social media engagement with Lego anti-burglar scenes
 Edinburgh police force builds social media engagement with Lego anti Edinburgh West Police have launched a social media campaign to inform web users how to avoid being burgled by building visual and educational scenes using Lego. The social media campaign was focused on raising awareness among Twitter users of […] .
Edinburgh police force builds social media engagement with Lego anti Edinburgh West Police have launched a social media campaign to inform web users how to avoid being burgled by building visual and educational scenes using Lego. The social media campaign was focused on raising awareness among Twitter users of […] .What happens when criminal law meets neuroscience?
 Robert J. Szczerba is the CEO of X Tech Ventures, an innovative company focused on solving some of today’s most challenging problems through the integration of technologies from multiple, diverse domains. This post originally appeared on Forbes. Transformative technology marks the progress of humanity. It also inevitably raises questions. […] .
Robert J. Szczerba is the CEO of X Tech Ventures, an innovative company focused on solving some of today’s most challenging problems through the integration of technologies from multiple, diverse domains. This post originally appeared on Forbes. Transformative technology marks the progress of humanity. It also inevitably raises questions. […] .Check out this insane video of virtual reality gaming made by Google-backed Magic Leap
 Magic Leap AR preview Magic Leap, the mysterious augmented reality startup with $542 million in funding by Google , just released a video that gives a glimpse into what its technology can do. Titled “Just another day in the office of Magic Leap,” the short clip shows augmented reality […] .
Magic Leap AR preview Magic Leap, the mysterious augmented reality startup with $542 million in funding by Google , just released a video that gives a glimpse into what its technology can do. Titled “Just another day in the office of Magic Leap,” the short clip shows augmented reality […] .The staggering reach of ISIS: Report reveals it has more than 46,000 Twitter accounts
 In this June 16, 2014 file photo, demonstrators chant pro-Islamic State group, slogans as they carry the group’s flags in front of the provincial government headquarters in Mosul, 225 miles (360 kilometers) northwest of Baghdad. A new report documenting the scale of the social media strategy of Islamic State […] .
In this June 16, 2014 file photo, demonstrators chant pro-Islamic State group, slogans as they carry the group’s flags in front of the provincial government headquarters in Mosul, 225 miles (360 kilometers) northwest of Baghdad. A new report documenting the scale of the social media strategy of Islamic State […] .The Face Detection Algorithm Set to Revolutionize Image Search
 Back in 2001, two computer scientists, Paul Viola and Michael Jones, triggered a revolution in the field of computer face detection. After years of stagnation, their breakthrough was an algorithm that could spot faces in an image in real time. Indeed, the so-called Viola-Jones algorithm was so fast and […] .
Back in 2001, two computer scientists, Paul Viola and Michael Jones, triggered a revolution in the field of computer face detection. After years of stagnation, their breakthrough was an algorithm that could spot faces in an image in real time. Indeed, the so-called Viola-Jones algorithm was so fast and […] .How tech can fight extremism
 Obama: Cyber threats challenge the nation’s security 02:01 Quintan Wiktorowicz served as President Obama’s senior adviser for countering violent extremism from 2011-2013 and is managing partner of Affinis Global , a strategy and communications consulting firm. Shahed Amanullah is an entrepreneur from Silicon Valley and principal at Affinis Global. […] .
Obama: Cyber threats challenge the nation’s security 02:01 Quintan Wiktorowicz served as President Obama’s senior adviser for countering violent extremism from 2011-2013 and is managing partner of Affinis Global , a strategy and communications consulting firm. Shahed Amanullah is an entrepreneur from Silicon Valley and principal at Affinis Global. […] .Marketing Opportunities for the Internet of Things
 The explosion of interest surrounding the Internet of Things presents a truly remarkable opportunity for marketing. The rise of internet-connected life, work and home is fueling growth and innovation across numerous industries–from communication services to manufacturing to healthcare. What caused the advent of the Internet of Things? A number of important technology changes have […] .
The explosion of interest surrounding the Internet of Things presents a truly remarkable opportunity for marketing. The rise of internet-connected life, work and home is fueling growth and innovation across numerous industries–from communication services to manufacturing to healthcare. What caused the advent of the Internet of Things? A number of important technology changes have […] .Egyptian Cyber Army: The hacker group attacking ISIS propaganda online
 There’s a new hacking group in cyberspace, and it’s going after the Islamic State ‘s online propaganda. Last week, less than 24 hours after ISIS social media accounts posted a threatening message from the group’s leader, the audio recording was replaced with a song and its transcript with a […] .
There’s a new hacking group in cyberspace, and it’s going after the Islamic State ‘s online propaganda. Last week, less than 24 hours after ISIS social media accounts posted a threatening message from the group’s leader, the audio recording was replaced with a song and its transcript with a […] .Security Threats Businesses Face on Social Media
 Security Threats Businesses Face on Social Media Social media has transformed the way businesses interact with customers. All at once it gives companies a new way to reach out to their fans while also giving the company a more personal touch. But as always seems to be the case, […] .
Security Threats Businesses Face on Social Media Social media has transformed the way businesses interact with customers. All at once it gives companies a new way to reach out to their fans while also giving the company a more personal touch. But as always seems to be the case, […] .'Sextortion' is an online 'epidemic' against children
 The number of complaints of online enticement of children is climbing. The Internet Crimes Against Children Task Force, which helps state and local law enforcement agencies fight online child pornography, reports that the number of complaints to its 61 offices nationwide has grown from 5,300 in 2010 to 7,000 […] .
The number of complaints of online enticement of children is climbing. The Internet Crimes Against Children Task Force, which helps state and local law enforcement agencies fight online child pornography, reports that the number of complaints to its 61 offices nationwide has grown from 5,300 in 2010 to 7,000 […] .Artist Gives First Responders Superhero Movie Poster Treatment
 As he got older, he began to realize that real-life superheros were all around him. The 30-year-old photographer decided to give police officers, firefighters, and emergency responders the kind of superhero treatment they deserved. Read Full Story Here .</ July 18, 2014 514 views Be the first to comment on this […] .
As he got older, he began to realize that real-life superheros were all around him. The 30-year-old photographer decided to give police officers, firefighters, and emergency responders the kind of superhero treatment they deserved. Read Full Story Here .</ July 18, 2014 514 views Be the first to comment on this […] .Must Reads: The Cyberbully Upstairs, Tweeting in Terror and More
 During the week, we consume words in snackable, tweetable bites. But on the weekends, we have the time to take a dive into the murkier, lengthier depths of the Internet and expand our attention spans beyond 140 characters. We can brew a cup of coffee and lie back with […] .
During the week, we consume words in snackable, tweetable bites. But on the weekends, we have the time to take a dive into the murkier, lengthier depths of the Internet and expand our attention spans beyond 140 characters. We can brew a cup of coffee and lie back with […] .Social media crimes account for HALF of police calls about abuse and anti-social behaviour, claims senior officer
 Around 6,000 officers are being specially-trained to deal with cyber crime Alex Marshall, head of the College of Policing says its a ‘real problem’ Claims the public are not aware of when an online insult becomes an offence He believes all investigations in the future will have an online […] .
Around 6,000 officers are being specially-trained to deal with cyber crime Alex Marshall, head of the College of Policing says its a ‘real problem’ Claims the public are not aware of when an online insult becomes an offence He believes all investigations in the future will have an online […] .Police Use Twitter, ‘Bait Bikes’ to Combat Theft
 In San Francisco , one Twitter account is watching over your bikes. Officer Matt Friedman of the San Francisco Police Department is behind the Anti-Bike Theft Unit , a program that utilizes Twitter and GPS trackers to thwart bike thefts in the city. The main tools in Friedman’s utility […] .
In San Francisco , one Twitter account is watching over your bikes. Officer Matt Friedman of the San Francisco Police Department is behind the Anti-Bike Theft Unit , a program that utilizes Twitter and GPS trackers to thwart bike thefts in the city. The main tools in Friedman’s utility […] .Why Invisible Activities Matter in Social Media
 Only 7% of word-of-mouth happens online . This is a key figure in understanding that leaving a digital footprint is part of a sophisticated process; diverse drivers explain why an idea goes online. For instance, when citizens want an idea to go public when it comes to a cause. […] .
Only 7% of word-of-mouth happens online . This is a key figure in understanding that leaving a digital footprint is part of a sophisticated process; diverse drivers explain why an idea goes online. For instance, when citizens want an idea to go public when it comes to a cause. […] .Morning Security Brief: Arkansas Tornado, Terrorism Concerns, Passport Security, and Hacking Satellites
► A powerful tornado in Arkansas carved an 80-mile path of destruction through an area around the Little Rock suburb of Vilonia, killing at least 16 people, possibly more, the Associated Press reports. Emergency officials began to pick through the rubble to look for survivors as the sun rose […] .Wi-fi hotspots: Europol warn over data theft
 Sensitive information should not be sent over public wi-fi hotspots, to avoid hackers stealing it, Europe’s top cybercrime police officer has warned. Troels Oerting, head of Europol’s cybercrime centre, told the BBC the warning was motivated by the growing number of attacks being carried out via public wi-fi. He […] .
Sensitive information should not be sent over public wi-fi hotspots, to avoid hackers stealing it, Europe’s top cybercrime police officer has warned. Troels Oerting, head of Europol’s cybercrime centre, told the BBC the warning was motivated by the growing number of attacks being carried out via public wi-fi. He […] .Major cyber attacks can be predicted, say researchers
 University of Michigan researchers have claimed that major international cyber attacks follow predictable patterns. A mathematical model could help understand the strategy and timing of attacks and predict the "next move" in conflicts, according to Robert Axelrod, professor of political science at the University. Axelrod likens the current state […] .
University of Michigan researchers have claimed that major international cyber attacks follow predictable patterns. A mathematical model could help understand the strategy and timing of attacks and predict the "next move" in conflicts, according to Robert Axelrod, professor of political science at the University. Axelrod likens the current state […] .Here's what an eavesdropper sees when you use an unsecured Wi-Fi hotspot | PCWorld
Click here to view original web page at www.pcworld.comThe Los Angeles Police Department Predicts and Fights Crime With Big Data
 When the movie Minority Report was released in 2002, the predicting and consequently preventing of crime was still science fiction. It was far away and criminals-to-be had not to fear about predictive analytics being used by the police. Fast-forward to 2014 and things have changed. Although we are still […] .
When the movie Minority Report was released in 2002, the predicting and consequently preventing of crime was still science fiction. It was far away and criminals-to-be had not to fear about predictive analytics being used by the police. Fast-forward to 2014 and things have changed. Although we are still […] .In the online hunt for criminals, social media is the ultimate snitch
 “I’d been looking for this robbery suspect. Detectives were at a dead end; I decide to look and see if the guy has Facebook. He does, completely unsecured, and had just ‘checked-in’ at a strip club. Search the lot, find a car matching the description of what he was seen […] .
“I’d been looking for this robbery suspect. Detectives were at a dead end; I decide to look and see if the guy has Facebook. He does, completely unsecured, and had just ‘checked-in’ at a strip club. Search the lot, find a car matching the description of what he was seen […] .Police Embrace Social Media
Police departments are increasingly embracing the idea of using social media sites, such as Facebook, for everything from soliciting crime tips to sharing safety-related information and improving community relations. The sites can give law enforcement an additional way to disseminate information quickly and to interact with the public. Through […] .Social Media: Establishing Criteria for Law Enforcement Use
 Mr. Stuart, a retired major with the Montgomery, Alabama, Police Department, is the assistant chief agent at the Alabama Criminal Justice Information Center. Over the past decade, social media has become a widespread presence that touches the lives of countless people, including law enforcement officers. Certain risks and rewards […] .
Mr. Stuart, a retired major with the Montgomery, Alabama, Police Department, is the assistant chief agent at the Alabama Criminal Justice Information Center. Over the past decade, social media has become a widespread presence that touches the lives of countless people, including law enforcement officers. Certain risks and rewards […] .Social Networking and Law Enforcement
 From Facebook to twitter , MySpace and LinkedIn , social media is changing the way business is done across the professional spectrum. This is particularly evident in the areas of criminology and criminal justice , where law enforcement officers and researchers alike are finding new and unique ways to […] .
From Facebook to twitter , MySpace and LinkedIn , social media is changing the way business is done across the professional spectrum. This is particularly evident in the areas of criminology and criminal justice , where law enforcement officers and researchers alike are finding new and unique ways to […] .Homeland Security struggles to tempt, retain cyber talent
Cyber attack “war game” to test London banks on November 12
LONDON (Reuters) - Thousands of staff across dozens of London financial firms will be put through a "war games" scenario on Tuesday to test how well they can handle a major cyber attack, people familiar with the matter said. In one of the largest exercises of its kind in [...]
Twitter UK boosts anti-abuse tools after threats against women

By Estelle Shirbon LONDON | Sat Aug 3, 2013 9:50am EDT LONDON (Reuters) - The British arm of Twitter apologized on Saturday to a group of high-profile women who have been threatened with death and rape on the micro-blogging site, and announced measures to make it easier for users [...]
Overcoming Fear: How to Break Through and Get Stuff Done

By Michael Stelzner Published August 2, 2013 Is fear holding you back in your business? Are you wondering what you can do to face your fears? To learn about the kinds of fears we deal with as marketers, I interview two small businesses owners for this 52nd episode of [...]
Russia’s leading social network banned by mistake
MOSCOW | Fri May 24, 2013 1:12pm EDT (Reuters) - Russia's leading online social network was briefly banned on Friday, in a move dismissed as a "mistake" but which follows intensifying official pressure on the company as President Vladimir Putin consolidates his power. VKontakte (www.vk.com), Europe's largest homegrown social [...]
Keeping your corporate social media accounts secure

Takeaway: Does your company have official social media accounts like Twitter or Facebook? How do you protect them from unauthorized access? Get a few tips here and take our poll on security measures. In the past few weeks, we have seen news stories about Twitter accounts of large organizations [...]
10 Ways Social Media is Transforming our Culture and World

It’s 2012, and yet I feel more calm about our future than ever before. The Internet has saved our asses, and we should celebrate. I’ve been on the Web for a long time, but every once in a while I have one of those tremendous moments when I have [...]
Google’s Inactive Account Manager heightens enterprise awareness for securing data

Takeaway: Preventing the commingling of company and personal data means focusing on securing the company data. Google’s new Inactive Account Manager feature has added options and predictability to the process of distributing digital assets when someone dies, or when someone simply stops using the service for a preset period [...]
Why are Indian women being attacked on social media?

What does a top woman journalist do when she is threatened regularly with gang rape and stripping on Twitter? And what about when her teenage daughter's name and details of her class and school are tweeted too? "It was very disturbing. I didn't know what to do. So for [...]
Twitter Hacks Force Companies to Confront Security on Social Media
While most Americans were winding up their holiday weekends last Monday, the phones at the Vancouver headquarters of HootSuite, a social media management company, began to ring. Burger King’s Twitter account had just been hacked. The company’s logo had been replaced by a McDonald’s logo, and rogue announcements began [...]
Social Media Led Authorities to a Benghazi Terror Suspect

It may be the biggest break in the international manhunt for the Benghazi killers and it's all thanks to social media. This morning, The Daily Beast's Eli Lake reports that Tunisian authorities are holding a man named Ali Ani al-Harzi suspected of participating in the Sept. 11 attacks that [...]
Click here to view full article
Hoe terroristen en criminelen social media en internet gebruiken

De UNDOC ( United Nations Office on Drugs and Crime) heeft eergisteren een enorm leerzaam 142 pagina’s tellend rapport over internet en social media gebruik voor en door criminelen. Facebook wordt onder andere gebruikt voor het verkrijgen van informatie omtrent doelen en veiligheidsprocedures die door mensen onbewust worden [...]
Click here to view full article
