Hotlittlepotato The shop has no sign. Or rather, the sign is obscured by some kind of bunting. The glass doors are papered over. You gotta know what’s back there, like a speakeasy. Venturing to open the door, I find I still can’t get inside. Between me and a cramped 180 square feet or so of convenience store-like shelves—yogurts, bags of exotically-flavored freeze-dried peas, refrigerators full of juice, and pre-packaged sandwiches—is a turnstile. It is a shop. I will shop. There’s a reader on the right. There’s an app. This is San Francisco, 2018. There is always an app. Get […] […]
Tag: data
Self-Driving Cars Should Look Down, Not Just Ahead
WaveSense ground penetrating radar tech comes out of MIT’s Lincoln Laboratory, a defense R&D center, and was first deployed to help troops navigate in Afghanistan in 2013. Self-driving cars are like snowbird retirees. Given the freedom to live, or operate, anywhere in the country, they turn their backs on wintry states and flock to the sun. There’s a reason Waymo, Uber, and even grocery story giant, Kroger, are testing their shiny new autonomous vehicles in southwestern cities like Phoenix. Yes, Arizona’s regulations are friendly to them, but the year-round good weather is the major draw. As sophisticated as these […] […]
The “neuropolitics” consultants who hack voters’ brains
Maria Pocovi slides her laptop over to me with the webcam switched on. My face stares back at me, overlaid with a grid of white lines that map the contours of my expression. Next to it is a shaded window that tracks six “core emotions”: happiness, surprise, disgust, fear, anger, and sadness. Each time my expression shifts, a measurement bar next to each emotion fluctuates, as if my feelings were an audio signal. After a few seconds, a bold green word flashes in the window: ANXIETY. When I look back at Pocovi, I get the sense she knows exactly […] […]
EU to fine social media platforms that take more than 1 hour to remove extremist content
The European Union is reportedly planning to impose stricter regulations on social media platforms including Facebook, YouTube , and Twitter over the removal of online terrorist propaganda. The Financial Times reported on Sunday that according to new draft regulations to be published next month, the EU plans to impose fines on companies if terrorist content is not deleted within an hour of posting, abandoning its earlier approach of getting internet platforms to remove such content voluntarily. The upcoming legislation builds on guidelines first prescribed by the EU in March for removal of radicalizing online content within one hour. Following […] […]
Distributed teams are rewriting the rules of office(less) politics
When we think about designing our dream home, we don’t think of having a thousand roommates in the same room with no doors or walls. Yet in today’s workplace where we spend most of our day, the purveyors of corporate office design insist that tearing down walls and bringing more people closer together in the same physical space will help foster better collaboration while dissolving the friction of traditional hierarchy and office politics. But what happens when there is no office at all? This is the reality for Jason Fried, Founder and CEO of Basecamp , and Matt Mullenweg, […] […]
Schools Are Mining Students’ Social Media Posts for Signs of Trouble
Aron Ontiveroz/The Denver Post/Getty Images Aaah, the traditions of a new school year. New teachers, new backpacks, new crushes—and algorithms trawling students’ social media posts. Blake Prewitt, superintendent of Lakeview school district in Battle Creek, Michigan, says he typically wakes up each morning to twenty new emails from a social media monitoring system the district activated earlier this year. It uses keywords and machine learning algorithms to flag public posts on Twitter and other networks that contain language or images that may suggest conflict or violence, and tag or mention district schools or communities. In recent months the alert […] […]
Technofobie of dreigende dystopie?
In China worden grote stappen gezet richting een maatschappij waarin burgers continu worden gevolgd, gemonitord en beoordeeld. Een sociale score moet ervoor zorgen dat men netjes wacht op het stoplicht, vaak op bezoek gaat bij familie en op tijd op het werk verschijnt. Overtredingen leveren strafpunten op en daarmee een lagere score waarmee je minder recht hebt op een goede baan of een appartement. Het is nu nog optioneel, maar in 2020 ontkomt de Chinese burger er niet meer aan. De Volkskrant schrijft in een artikel over de Chinese technologie dat wij, in het westen, nog ‘huiverig’ zijn qua […] […]
Google gebruikt Artificial Intelligence voor het koelsysteem in het datacenter
Datacenters moeten koel zijn, om de servers goed te laten functioneren. De afgelopen jaren werkte Google aan een Artificial Intelligence algoritme die zich kan aanpassen aan een koelsysteem. Koelsysteem Google Nu heeft het algoritme alles onder controle in Google’s datacenter. De AI heeft geleerd om de temperatuur zo optimaal mogelijk te houden, maar wel energie te besparen. De besparing is ongeveer veertig procent. In eerste instantie werden de aanbevelingen van het systeem eerst bekeken en daarna toegepast. Dat kostte veel tijd, en uiteindelijk hebben ze het systeem geautomatiseerd. Er zijn wel altijd opzichters die het systeem in de gaten […] […]
Hubble Captures 15,000 Galaxies in a Single Stunning Image
Early in Hubble’s mission, it scanned a patch of sky for 10 days to collect 342 separate images. When assembled, they became the now-famous Hubble Deep Field. NASA has updated this iconic image over the years as the telescope became more powerful, and it’s doing so again. Hubble may be inching toward obsolescence with the upcoming launch of the James Webb Space Telescope (JWST), but it’s still producing amazing images. The newest panoramic view of the universe shows more galaxies than ever before . According to NASA, the new image features a whopping 15,000 galaxies, and 12,000 of them […] […]
Smart irrigation systems vulnerable to attacks, warn researchers
Security researchers have warned of a potential attack that – using a “piping botnet ” of internet-connected irrigation systems that water simultaneously – could impact a city’s water system to the point of actually draining its reserves. A team of six academics from Ben-Gurion University of Negev, Israel, identified and analyzed security flaws in the firmware of several commercial irrigation systems that are connected to the internet. They focused on three commonly sold smart irrigation systems – GreenIQ, BlueSpray, and RainMachine – and found that they suffer from vulnerabilities that enable attackers to remotely turn watering systems on and […] […]
Eng: Facebook volgt je op nóg veel meer manieren dan je denkt
Dat we op de voet gevolgd worden door Facebook is inmiddels alom bekend, maar nu dat de social media-gigant antwoord heeft gegeven op vragen die in het Amerikaanse congres zijn gesteld blijkt dat het allemaal nog veel verder gaat dan we allemaal dachten. Dit zijn een aantal van de manieren waarop Mark Zuckerberg & Co. ons volgen op het internet, allemaal gehaald uit het document van 222 pagina’s dat is doorgestuurd naar het Congres. Een gedeelte van deze tracking-methodes kenden we al, maar als je het allemaal achter elkaar zet zul je zien dat er heel weinig geheim blijft […] […]
Een film die je kunt sturen met je brein
Aan de universiteit van Nottingham hebben ze iets voor elkaar gekregen wat in eerste instantie lijkt op een goed science fiction verhaal. Waar je normaal gesproken in de bioscoopzaal of op de bank een film kijkt waarvan de slotscène al lang en breed vastligt, kun je nu ook een film kijken die nog alle kanten op kan gaan. De film ‘The Moment’ vormt zich naar de toestand van je brein. Dit zit zo. De activiteit in je brein wordt gemeten met EEG, middels een headset die het hoofd is bevestigd. Hiermee kan gekeken worden of je bijvoorbeeld slaapt, ontspannen […] […]
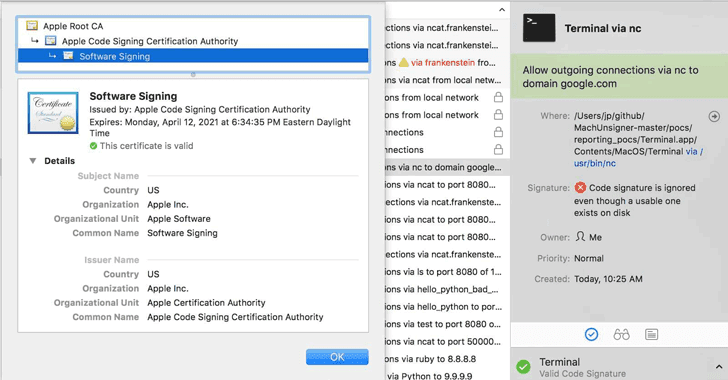
Signature Validation Bug Let Malware Bypass Several Mac Security Products
A years-old vulnerability has been discovered in the way several security products for Mac implement Apple’s code-signing API that could make it easier for malicious programs to bypass the security check, potentially leaving millions of Apple users vulnerable to hackers. Josh Pitts, a researcher from security firm Okta, discovered that several third-party security products for Mac—including Little Snitch, F-Secure xFence, VirusTotal, Google Santa, and Facebook OSQuery—could be tricked into believing that an unsigned malicious code is signed by Apple. Code-signing mechanism is a vital weapon in the fight against malware, which helps users identify who has signed the app […] […]
MIT’s New AI Can See Through Walls
MIT has given a computer x-ray vision, but it didn’t need x-rays to do it. The system, known as RF-Pose, uses a neural network and radio signals to track people through an environment and generate wireframe models in real time. It doesn’t even need to have a direct line of sight to know how someone is walking, sitting, or waving their arms on the other side of a wall . Neural networks have shown up in a lot of research lately when researchers need to create a better speech synthesis model, smarter computer vision, or an AI psychopath . […] […]
Robots Won’t Take Your Job—But They Might Make It Boring
Robert Deyrail/Getty Images Whether they believe robots are going to create or destroy jobs, most experts say that robots are particularly useful for handling “dirty, dangerous and dull” work. They point to jobs like shutting down a leaky nuclear reactor , cleaning sewers , or inspecting electronic components to really drive the point home. Robots don’t get offended, they are cheap to repair when they get “hurt,” and they don’t get bored. It’s hard to disagree: What could possibly be wrong about automating jobs that are disgusting, mangle people, or make them act like robots? The problem is that […] […]
Cognitive diversity and marketing: How AI is improving innovation
NASA employee George Washington handles clerical work more quickly and efficiently than ever before. He never complains about working late hours and he never needs to stop for a coffee break. Washington is a bot who takes in information from emails and identifies job candidate suitability — something formerly completed by human resources personnel. He represents a new type of diversity within organizations, cognitive diversity. Cognitive diversity, simply put, includes different ways of thinking. It consists of both humans (cognitive thinking) and machines (cognitive technologies). Today, automation is pouring into the workplace at an accelerating rate. Cognitive technologies involve: […] […]
With its new in-car operating system, BMW slowly breaks with tradition
When you spend time with a lot of BMW folks, as I did during a trip to Germany earlier this month, you’ll regularly hear the word “ heritage .” Maybe that’s no surprise, given that the company is now well over 100 years old. But in a time of rapid transformation that’s hitting every car manufacturer, engineers and designers have to strike a balance between honoring that history and looking forward. With the latest version of its BMW OS in-car operating system and its accompanying design language, BMW is breaking with some traditions to allow it to look into […] […]
Apple is closing a loophole that lets police hack into iPhones
It’s a win for privacy advocates, but it’s sure to enrage law enforcement officials by making it harder than ever for them to get information out of locked phones. The news: Apple plans to send out a software update to iPhone users that will make the smartphone’s charging and data port inoperative an hour after the phone has been locked. Though you’ll still be able to charge a phone without tapping in a password, you’ll now need one to pull data off it via that port. Why it matters: Apple has a history of fighting law enforcement efforts to […] […]
A few big players may have been behind Bitcoin’s huge surge last year
New research (PDF) suggests that a price manipulation scheme may have been behind the cryptocurrency’s extraordinary rally in 2017. The study: Researchers at the University of Texas analyzed blockchain data and found that large purchases of cryptocurrency from multiple trading platforms in exchange for Tether, a crypto-token that’s supposedly pegged to the US dollar , were “timed following market downturns” and, since cryptocurrency prices tend to move as one, resulted in “sizable increases in Bitcoin prices.” This suggests, according to the New York Times , that a few players may have been propping up the price of Bitcoin and […] […]
Microsoft Issues Emergency Patch For Critical Flaw In Windows Containers
Just a few days prior to its monthly patch release, Microsoft released an emergency patch for a critical vulnerability in the Windows Host Compute Service Shim (hcsshim) library that could allow remote attackers to run malicious code on Windows computers. Windows Host Compute Service Shim (hcsshim) is an open source library that helps “Docker for Windows” execute Windows Server containers using a low-level container management API in Hyper-V. Discovered by Swiss developer and security researcher Michael Hanselmann , the critical vulnerability (tracked as CVE-2018-8115) is the result of the failure of the hcsshim library to properly validate input when […] […]