Onderzoekers van Universiteit Leuven en het Imperial College Londen hebben ontdekt dat het de-anonimiseren van geanonimiseerde datasets makkelijker is dan tot voor kort werd aangenomen . Ze hebben dit aangetoond door middel van een model dat schat hoe makkelijk het is om een dataset te de-anonimiseren. Geanonimiseerde gegevens worden overal voor gebruikt: medisch onderzoek, gepersonaliseerde aanbevelingen en moderne AI-technieken. De veronderstelling is dat alle persoonlijke identificeerbare informatie verwijderd is terwijl een kern van de nuttige informatie voor onderzoekers behouden blijft. Zo heeft een ziekenhuis de mogelijkheid om de namen, adressen en geboortedata van patiënten te verwijderen uit een set […] […]
Category: Social Media & Crime
Ransomware and the enterprise: A new white paper
Throughout 2018 criminals have continued to target large organizations with ransomware. Today we introduce a new white paper that explains why ransomware is still a serious threat to your organization – regardless of size – and what can be done to reduce exposure to, and damage from, ransomware attacks. The paper focuses on three particularly dangerous ransomware attack vectors: remote access, email, and supply chain. The paper is intended to help CEOs, CIOs, CISOs, and enterprise risk managers understand the current state of the ransomware threat as well several evolving areas of concern. The more technical aspects of ransomware […] […]
Before Using Birth Control Apps, Consider Your Privacy
Hotlittlepotato Score one for the quantified self-surveillance movement. Last week, the US Food and Drug Agency approved the first-ever, over-the-counter digital contraceptive—a polished and almost preternaturally upbeat mobile app called Natural Cycles . Basal body temperature readings and monthly menstruation data feed into an algorithm that tells users whether or not they should be having unprotected sex. Like most forms of birth control, it’s not foolproof ; the app has been dogged by reports of unwanted pregnancies that prompted two ongoing investigations by European authorities into its Swedish maker’s marketing claims. But that hasn’t hurt Natural Cycles’ popularity. The […] […]
How to Protect Yourself Against a SIM Swap Attack
Casey Chin A spate of hacked Instagram accounts. A $220 million lawsuit against AT&T. A bustling underground crime ring . They all have roots in an old problem that has lately found new urgency: SIM card swaps , a scam in which hackers steal your mobile identity—and use it to upend your life . At its most basic level, a SIM swap is when someone convinces your carrier to switch your phone number over to a SIM card they own. They’re not doing it for prank call cover, or to rack up long-distance charges. By diverting your incoming messages, […] […]
Smart irrigation systems vulnerable to attacks, warn researchers
Security researchers have warned of a potential attack that – using a “piping botnet ” of internet-connected irrigation systems that water simultaneously – could impact a city’s water system to the point of actually draining its reserves. A team of six academics from Ben-Gurion University of Negev, Israel, identified and analyzed security flaws in the firmware of several commercial irrigation systems that are connected to the internet. They focused on three commonly sold smart irrigation systems – GreenIQ, BlueSpray, and RainMachine – and found that they suffer from vulnerabilities that enable attackers to remotely turn watering systems on and […] […]
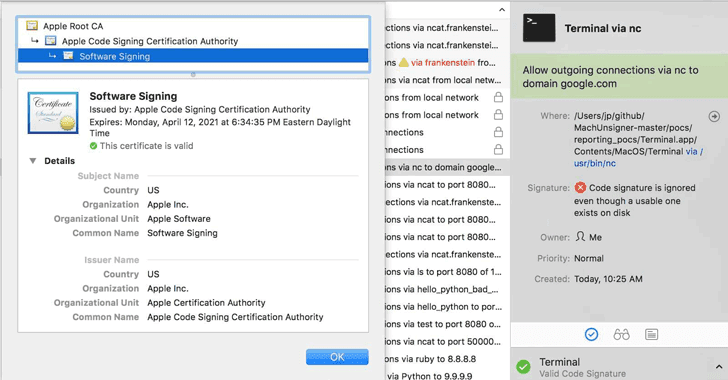
Signature Validation Bug Let Malware Bypass Several Mac Security Products
A years-old vulnerability has been discovered in the way several security products for Mac implement Apple’s code-signing API that could make it easier for malicious programs to bypass the security check, potentially leaving millions of Apple users vulnerable to hackers. Josh Pitts, a researcher from security firm Okta, discovered that several third-party security products for Mac—including Little Snitch, F-Secure xFence, VirusTotal, Google Santa, and Facebook OSQuery—could be tricked into believing that an unsigned malicious code is signed by Apple. Code-signing mechanism is a vital weapon in the fight against malware, which helps users identify who has signed the app […] […]
World’s biggest DDoS marketplace taken down, six suspected admins nabbed
An international law enforcement operation has shut down a website widely thought to be the world’s biggest marketplace for hiring distributed denial-of-service ( DDoS ) attacks, according to an announcement by the United Kingdom’s National Crime Agency (NCA). The website, webstresser.org, was taken down on Wednesday, April 25, following […] .
AI Can Help Cybersecurity—If It Can Fight Through the Hype
There are a ton of claims around AI and cybersecurity that don’t quite add up. Here’s what’s really going on. Walking the enormous exhibition halls at the recent RSA security conference in San Francisco, you could have easily gotten the impression that digital defense was a solved problem. Amidst […] .
Data Protection Standards Need to Be Global
Broadly, customers around the world should be in charge of the information companies have about them, and companies need to be liable if they misuse it. Whether it is Cambridge Analytica gaining access to private information on up to 87 million Facebook users, or the large-scale data breaches at […] .
This test will tell you how likely you are to fall for fraud
Researchers have devised a test that gauges a person’s susceptibility to falling for online scams and other types of internet crime. The freely available questionnaire – called “ Susceptibility to Persuasion – II ” (StP-II) and developed by scientists at the Universities of Cambridge and Helsinki – asks the […] .
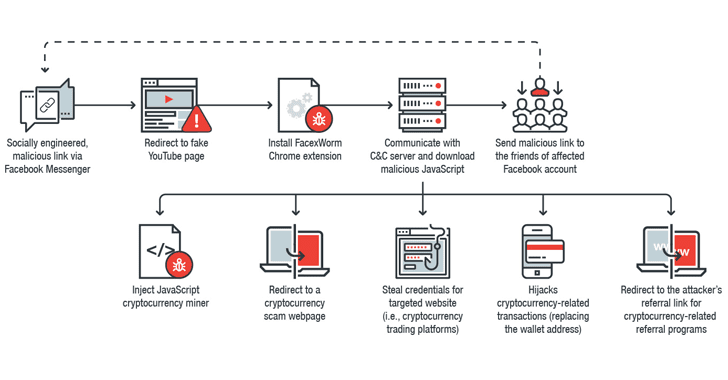
A New Cryptocurrency Mining Virus is Spreading Through Facebook
If you receive a link for a video, even if it looks exciting, sent by someone (or your friend) on Facebook messenger—just don’t click on it without taking a second thought. Cybersecurity researchers from Trend Micro are warning users of a malicious Chrome extension which is spreading through Facebook […] .
Have we hit peak ransomware? Maybe, according to F-Secure
Ransomware is really nasty. Once it’s infiltrated your system, it’ll place your crucial work files and cherished family photos out of reach, and demand a small fortune in Bitcoin for their return. Fortunately though, new research from Finnish security firm F-Secure suggests that this is a threat that’s hit […] .
Amazon Key Lets Delivery People Into Your House—and It Just Got Hacked
Today Amazon Key Lets Delivery People Into Your House—and It Just Got Hacked A key hardware safeguard in Amazon’s recently launched while-you’re-out delivery service has been hacked. And, well—less just say you probably should have seen this coming. Amazon Key uses a smart lock and cloud-based security camera in […] .
Nederlandse kansspelautoriteit onderzoekt games met ‘lootboxen’
Het is het laatste jaar een steeds groter wordende klacht bij gamers: lootboxen. Voor wie niet speelt: zie het als een pakje verzamelkaarten, met het verschil dat de kaarten iets doen in een game waar je als speler iets aan hebt. Dat varieert van cosmetische attributen zoals bijvoorbeeld een […] .
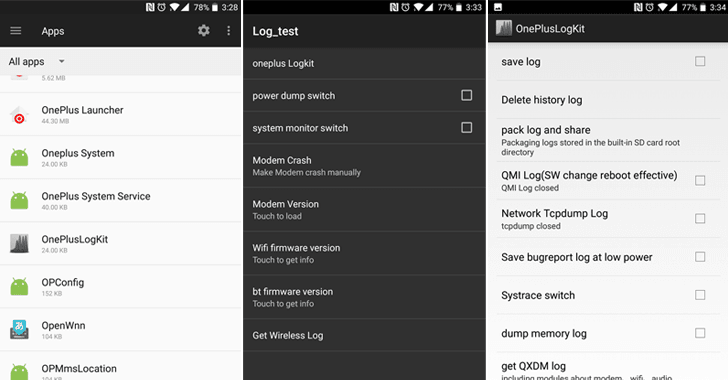
Another Shady App Found Pre-Installed on OnePlus Phones that Collects System Logs
The OnePlus Saga Continues… Just a day after the revelation of the hidden Android rooting backdoor pre-installed on most OnePlus smartphones, a security researcher just found another secret app that records tons of information about your phone. Dubbed OnePlusLogKit , the second pre-installed has been discovered by the same […] .
Latest NSA Leak Reveals Exactly the Kind of Cyberattack Experts Had Warned About
The details of an apparent Russian state-sponsored cyberattack on local election officials and a vendor of U.S. voting software are shocking—but they shouldn’t be surprising. In fact, experts had been warning for months before the 2016 election about exactly the type of attack that was revealed Monday in leaked […] .
Newly Found Malware Uses 7 NSA Hacking Tools, Where WannaCry Uses 2
A security researcher has identified a new strain of malware that also spreads itself by exploiting flaws in Windows SMB file sharing protocol, but unlike the WannaCry Ransomware that uses only two leaked NSA hacking tools , it exploits all the seven. Last week, we warned you about multiple […] .
The 5 most common online scams to watch for
The internet can be a scary place. Misinformation, false promises, and fake news lurk behind every clickbait headline and questionable link. Entire industries are built to profit from deceptive tricks to con the naive […] .
Hackers Are Trying to Reignite WannaCry With Non-Stop Botnet Attacks
Over the past year, two digital disasters have rocked the internet. The botnet known as Mirai knocked a swath of major sites off the web last September, including Spotify, Reddit, and the New York Times . And over the past week, the WannaCry ransomware outbreak crippled systems […] .
Another Ransomware Nightmare Could Be Brewing in Ukraine
Just as the reverberations from last week’s WannaCry ransomware outbreak have started to slow, a new threat has already cropped up. A virulent ransomware strain called XData has gained momentum in Ukraine, so far leading to about three times as many infections as WannaCry did in the […] .